
2-factor authentication (2FA) keeps your online accounts safe by requiring more than just your password to log in. But there are a variety of different 2FA methods to choose from, so how do you know which one is right for you? Here I’ll give you the low-down on each method to help you decide.
There are five common 2FA methods: SMS, email, push notifications, authenticator apps, and security keys. For each of these methods, I’ll address the following questions: 1) Is it supported by most services? 2) How secure is it? 3) How convenient is it to use? 4) Does it work offline? 5) Can you use it without extra hardware or software? 6) Is it free?
For those of you who just want a quick summary, you can check out the infographic below or download a high quality version of it here. Otherwise, let’s get started!
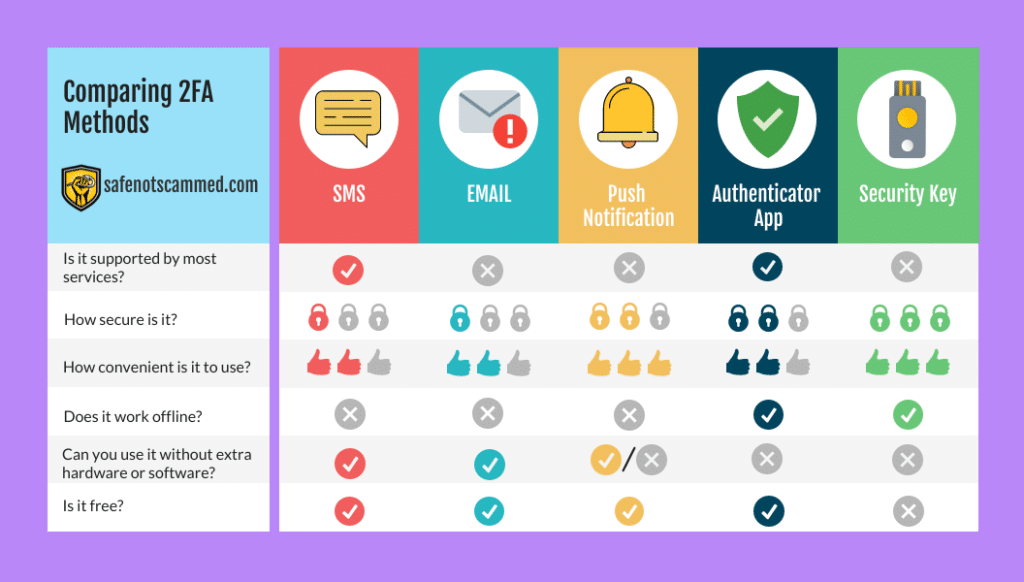
Table of Contents
- Method #1: SMS
- Method #2: Email
- Method #3: Push Notification
- Method #4: Authenticator App
- Method #5: Security Key
- The Takeaway
Method #1: SMS

With SMS-based 2FA, you’re sent a code via text message that you need to enter to complete the login process.
Is SMS-based 2FA supported by most services?
Yes. SMS is by far the most commonly supported form of 2FA, as you can see by looking at the entries in 2fa.directory. However, a few services, like social media site Reddit and email provider Hey, do not offer this method of 2FA.
SMS-based 2FA is probably so widely offered because almost everyone has access to a phone capable of receiving text messages. It is also often the only form of 2FA supported by certain services, particularly banks, which is unfortunate because it is not the most secure method.
How secure is it?
While SMS-based 2FA is much better than no 2FA at all, it’s unfortunately not very secure.
Hackers can gain access to your 2FA codes sent via text by stealing your phone number in what’s known as a SIM-swap attack. If they already know your password, perhaps due to a data breach, they can immediately take over your online accounts.

If the hackers don’t already know your password, they still have options. Many online services allow you to reset your password via text. If that’s the case for your accounts, the hackers can just reset your password.
SMS-based 2FA can also be bypassed by phishing and the codes can be stolen via malware.
How convenient is it to use?
SMS-based 2FA is reasonably convenient. Most of us keep our phones close by at all times, so needing it to log in to our accounts isn’t too much of a hassle. But sometimes it can take a while for the 2FA texts to arrive, which is annoying. And actually typing the 2FA code into a website can be irritating as well, especially if you make a typo or misread it and have to do it again.
Does it work offline?
To receive 2FA codes via text, you either need cell service or a Wi-Fi connection and a phone with Wi-Fi calling enabled. So you need some kind of connection for SMS-based 2FA to work. This can be a pain, especially when traveling.
Can you use it without extra hardware or software?
Yes, SMS-based 2FA just requires a phone with texting capabilities.
Is it free?
Yes, so long as you have a phone plan that includes text messages.
Method #2: Email
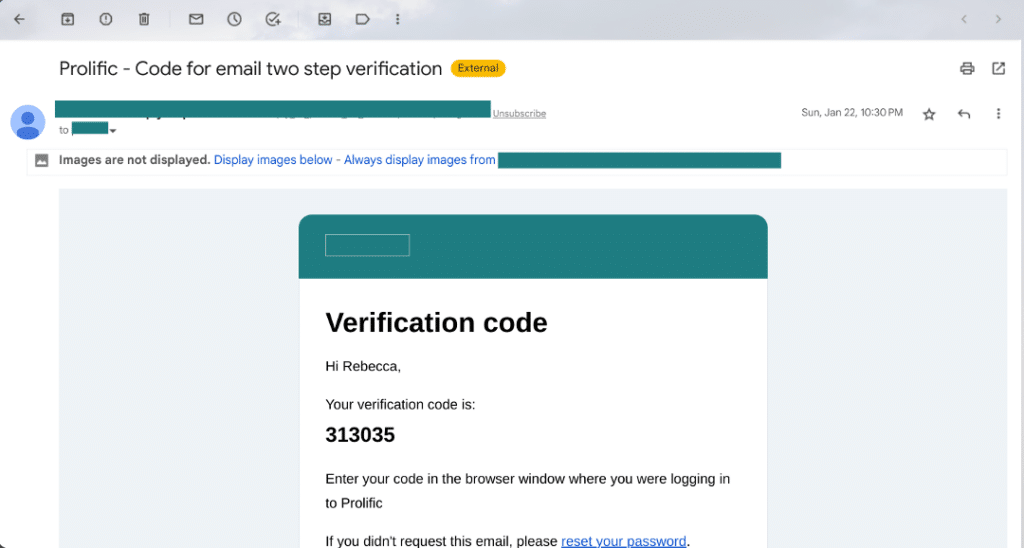
With email-based 2FA, you’re sent a one-time code via email that you need to use to complete the login process
Is email-based 2FA supported by most services?
No, many services do not offer email based 2FA, as you can see from 2fa.directory. That being said, it appears to be more widely offered among gaming sites.
Is it secure?
Email-based 2FA is arguably more secure than SMS-based 2FA, as it’s not vulnerable to SIM-swap attacks.
However, if your email is not secured with a strong password and a secure form of 2FA, hackers can break into your email account and steal your 2FA codes. As many services allow you to reset your password via email, once they’ve got access to your email, they can reset the passwords for your other accounts as well.
Email-based 2FA can also be bypassed via phishing.
How convenient is it to use?
So long as you have easy access to your email, email-based 2FA will be relatively convenient. However, you’ll need to wait for the 2FA code to arrive in your inbox, which can be frustrating when it takes a while. Once it’s arrived, you’ll need to type the code into the website, which is a minor irritation.
Does it work offline?
Nope, you need to be connected to the internet to receive 2FA codes sent via email. This can be a problem when traveling.
Can you use it without extra hardware or software?
Yep, email-based 2FA just needs an active email account.
Is it free?
Yes, email-based 2FA is free.
Method #3: Push notifications
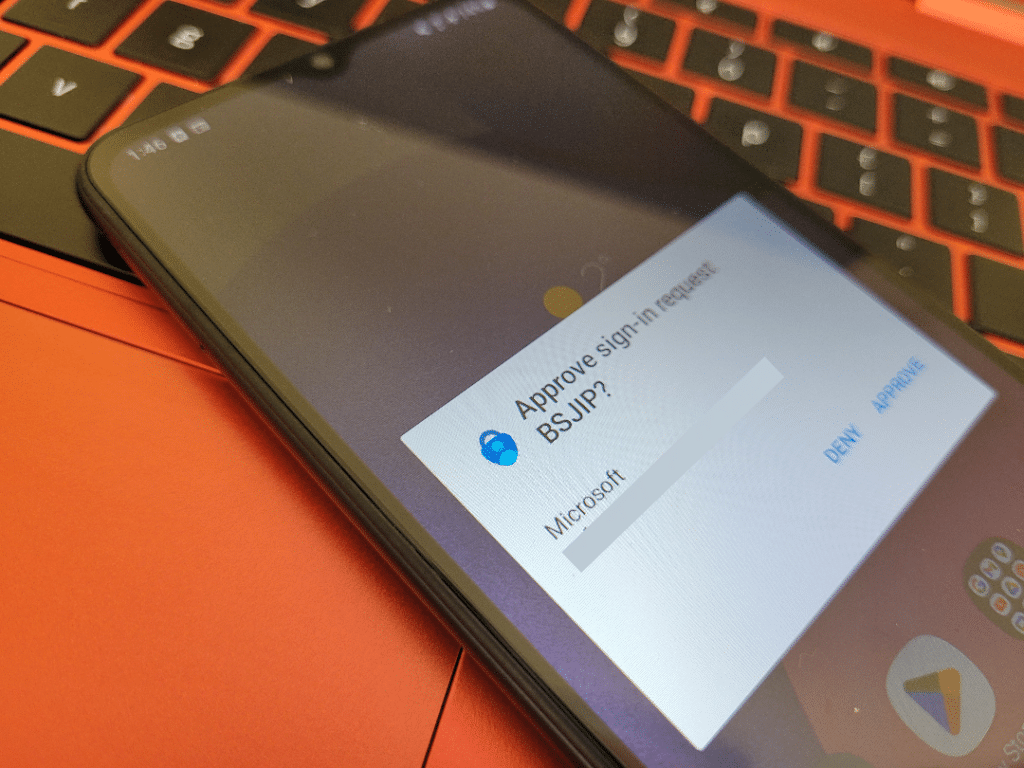
With push-based 2FA, you receive a notification on your smartphone that you must approve to complete the login process.
Is push-based 2FA supported by most services?
It’s not supported by many services and doesn’t even have its own category on 2fa.directory. However, some big companies like Google and Microsoft offer it.
How secure is it?
Push-based 2FA is more secure than SMS-based 2FA as it’s not susceptible to SIM-swap attacks. It’s also arguably more secure than email-based 2FA, since it should be harder for most hackers to steal your phone than break into your email.
However, push-based 2FA is still vulnerable to phishing. It is also susceptible to prompt-bombing attacks.

In a prompt-bombing attack, a hacker has already stolen your password, perhaps from a data breach, and they continually enter your credentials to try to log in to your account. Each such attempt generates a push notification on your phone. Eventually, you may accept one of those notifications, either by mistake or just to make them stop, and end up giving the hacker access to your account.
Fortunately, this type of attack can be prevented by number matching. When number matching is enabled, a 2FA push notification will require you to either select or type in a code displayed on the website you’re trying to log in to. If you’re not the one logging in, you then won’t know the code needed to approve the login, meaning you can’t approve a notification by mistake.
How convenient is it to use?
Push-based 2FA is very easy to use as you just need to tap to approve or reject the notification on your phone. It’s a little more complicated when number matching is enabled, but if you need to enter a code, it’s only usually 2 digits long.
Can you use it offline?
No, you’ll need an internet connection to use push-based 2FA.
Can you use it without extra hardware or software?
It depends. Some services, like Google and GitHub, will send you 2FA push notifications so long as you are signed in to one of their apps on your device. Other services, however, may require you to download an additional app, like Duo, to handle the push notifications.
Is it free?
Yes, push-based 2FA is free.
Method #4: Authenticator apps
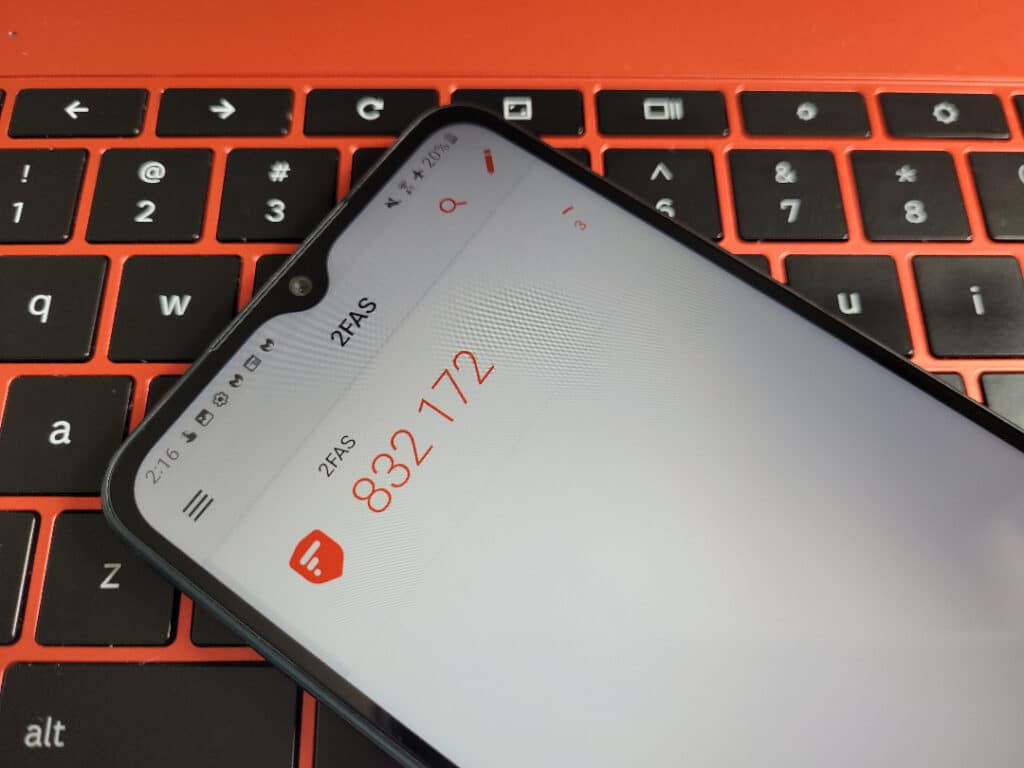
With authenticator-based 2FA, you install an app on your phone that you link to your online accounts. When you log in, you’ll need to enter a 6 digit code generated by the app.
Is authenticator-based 2FA supported by most services?
Many services that offer 2FA now support authenticator apps. Unfortunately, banks are an exception, with many still only offering SMS-based 2FA.
How secure is it?
Authenticator based 2FA is a solid choice from a security perspective. It is not susceptible to SIM-swaps or prompt-bombing attacks. However, it is susceptible to phishing, and authenticator codes can also be stolen by malware.
How convenient is it to use?
Authenticator apps are relatively convenient to use. When asked to enter the code to authenticate your login, you open the app and type the displayed code into the website. Typing the code in can be frustrating, however, as sometimes it will expire while you’re in the middle of typing it, since each code only lasts for 30 seconds.
Does it work offline?
Yes, authenticator apps work offline, so you can use them without a Wi-Fi connection or your phone’s data. This is useful if you need to access your accounts while traveling.
Can you use it without extra hardware or software?
No, authenticator-based 2FA requires you to download an app that you use to generate your 2FA codes. However, you can use that same app for all your accounts.
Is it free?
Yes, most authenticator apps, including Google Authenticator, Microsoft Authenticator and Authy, are free.
Method #5: Security keys

With security key-based 2FA, you have a small USB drive-like device that you plugin and tap to complete the login process.
Is security key-based 2FA supported by most services?
No, security keys are not yet supported by most services. However, more services are offering them as an option. For example, Apple recently added support for security keys.
How secure is it?
2FA with a hardware security key is the gold standard for security. It is not susceptible to SIM-swaps or prompt bombing and is the only form of 2FA that offers protection against phishing. That’s because the security key knows if you’re on a phishing site. If you are, it won’t work, preventing the attackers from taking over your account.
How convenient is it to use?
Using a security key is actually very convenient. To log in, all you need to do is plug the security key into your device (or connect it using NFC) and tap a button on the key. That’s it!
Does it work offline?
Yes, a security key works offline. You just need to plug it into your device and you’re ready to go!
Can you use it without extra hardware or software?
No. To use this form of 2FA, you’ll need a security key, which is a physical device that looks like a USB drive.
Is it free?
Unfortunately, security keys are not free. Not only that, some of them can be expensive. The cheapest ones I’ve found cost around $18, but the more expensive models can cost upwards of $50 each.
The takeaway
Deciding which form of 2FA to use can feel overwhelming. But don’t give up and decide not to turn it on at all! Any form of 2FA will protect your accounts far better than just a password alone.
That said, I’d recommend against SMS-based 2FA if possible. Instead, consider using an authenticator. Authenticators provide solid security and are widely supported, making them a great choice for most people. If you want extra protection, a security key is a worthwhile investment if you use services that support them.
