Last updated on March 3rd, 2023 at 03:55 am
A couple of weeks ago, I found myself wondering what the most popular form of two-factor authentication (2FA) is.
Is it the least secure but temptingly convenient SMS-based 2FA that sends you a code via text? Or the more secure but somewhat cumbersome authenticator app that generates codes on your phone? What about the ultra-secure but more expensive hardware key that lets you verify your identity with the tap of a button?
I tried asking on Twitter, but as I’m not exactly a social media influencer, my poll received a paltry seven votes. So, I decided to pony up $30 and run a quick study on the survey platform Prolific to reach more people.
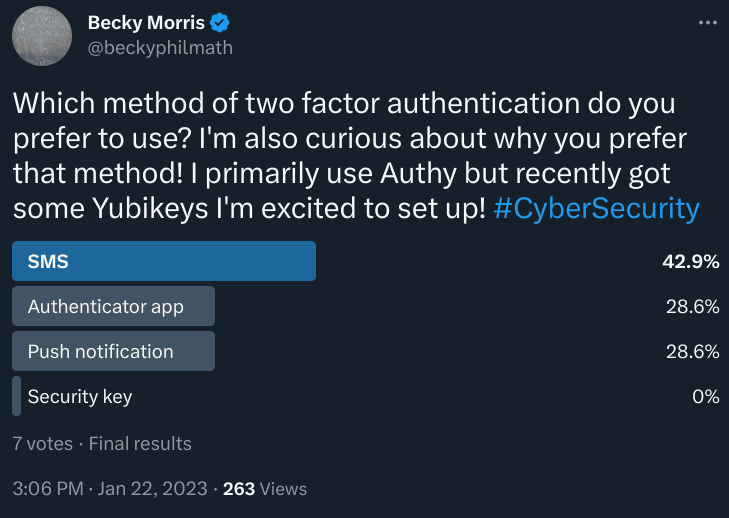
$30 bought me 26 survey takers, which is much better than seven, but not exactly enough to draw any rigorous conclusions. Still, it’s sufficient to see some trends emerge and the results seem in line with my tiny Twitter poll.
Survey results
First, I asked the survey takers whether they use 2FA on at least one account. The answer was a pleasant surprise: everyone did.
Then I asked the participants for their preferred 2FA method out of SMS, email, authenticator app, push notification, and security key.
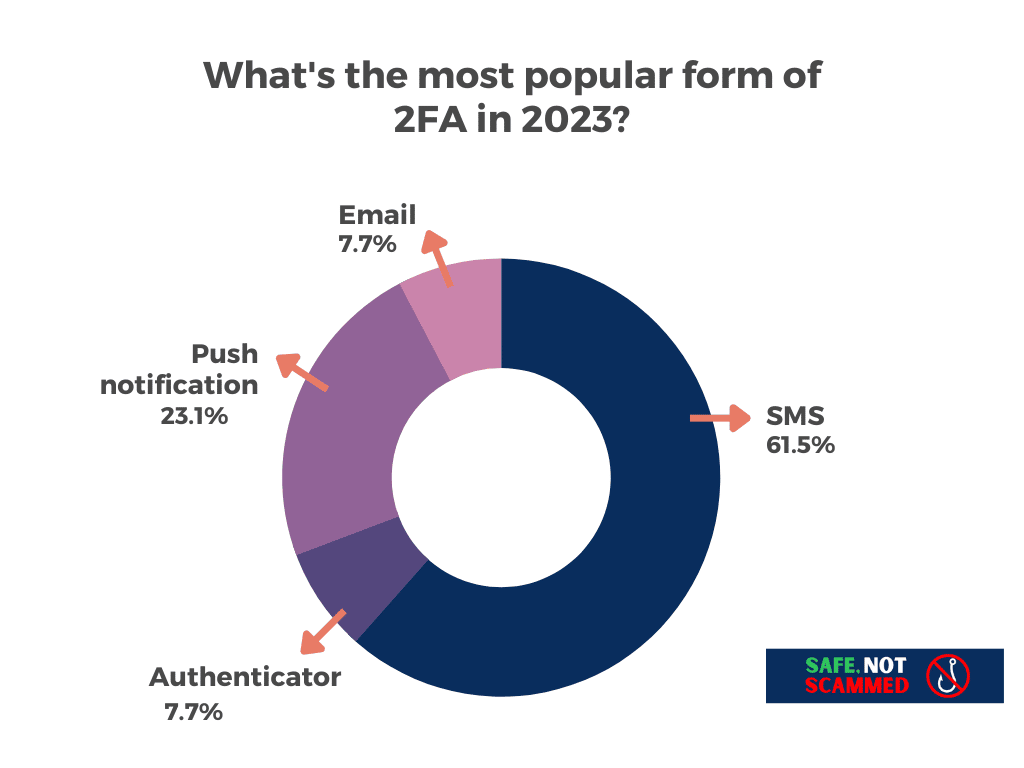
Perhaps not surprisingly, SMS reigned supreme, with a whopping 61.5% of the vote. Survey takers said they preferred this method because of how fast and easy it is to use.
Push notifications were the next most popular option, though they received just 23.1% of the vote. Authenticator apps and email were tied for third place, with 7.7% of the votes each. A little disappointingly, security keys received no votes at all.
I also asked the survey takers if they were familiar with four ways cybercriminals can bypass 2FA: SIM swaps, prompt bombing (also called push bombing), phishing, and cookie hijacking malware.
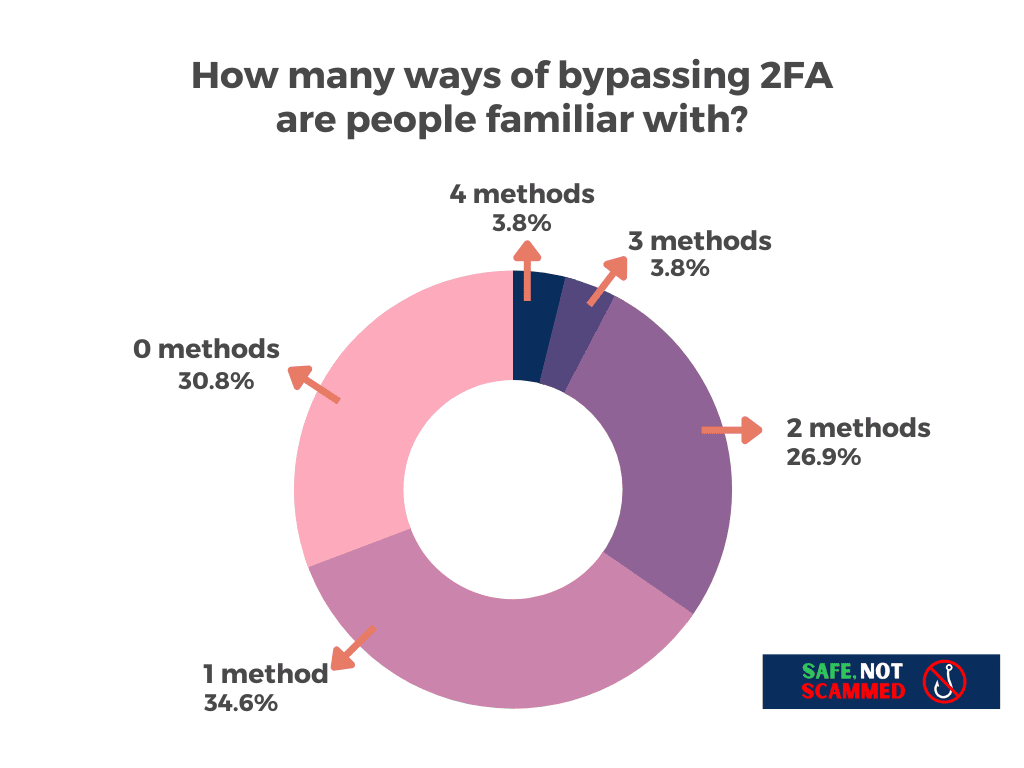
Most were relatively unaware of these methods. 30.8% reported being familiar with none of them, while 34.6% were familiar with just one. And although 26.9% were aware of two different techniques, just 3.8% had heard of three and 3.8% had heard of all 4.
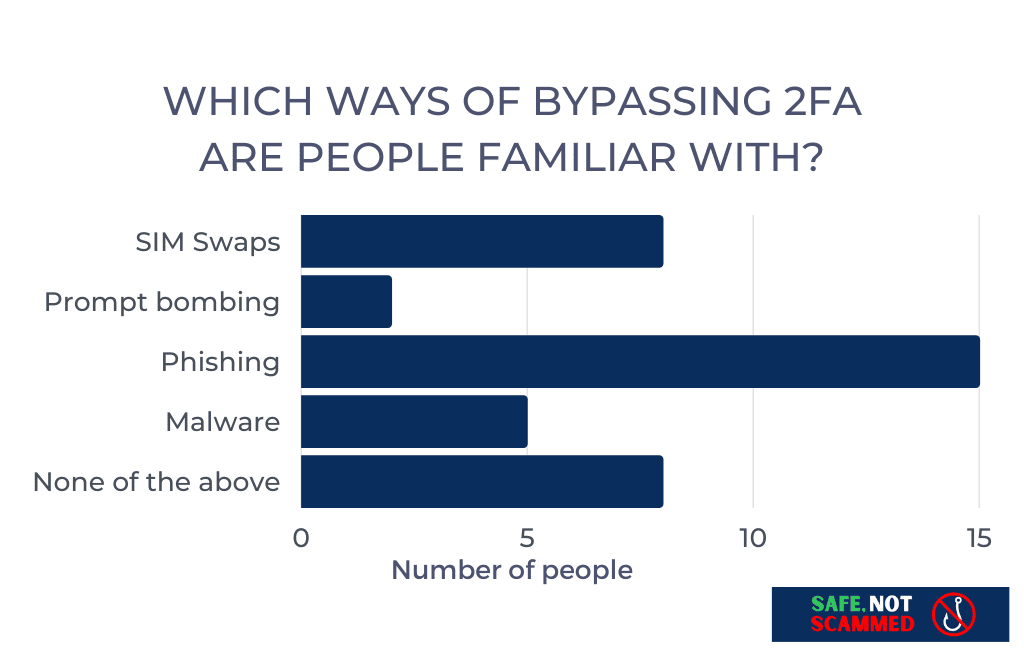
Phishing was the most well-known method of 2FA bypass, with 57.7% of survey takers reporting being familiar with it.
Despite SIM-swapping making the news thanks to high-profile victims like Jack Dorsey, only 30.8% of survey takers indicated they had heard of it.
Cookie hijacking malware, which has been gaining in popularity in recent years, was familiar to just 19.2% of survey takers.
Prompt bombing, which made the news last year thanks to the antics of hacking collective Lapsus$, was the least well-known, with only 7.7% of survey takers being aware of this technique.
Thoughts on the survey results
While any form of 2FA is better than none, it’s concerning that such a large proportion of people prefer SMS-based 2FA. Security experts have been warning for years that it’s insecure, and recent data breaches, like those at T-Mobile, make it easier for cybercriminals to carry out SIM-swaps and steal 2FA codes sent via text.
It’s also worrying that most people are not aware of the common ways cybercriminals can bypass 2FA. A lack of familiarity with these attacks means people are not in a good position to defend themselves and their accounts.
The takeaway
If you’re one of the majority of people who rely on SMS-based 2FA, consider trying out an alternative method, at least for high-value accounts. Authenticator apps, like Authy, are a good option for most people, though for maximum security a security key is the way to go.
Finally, it’s worthwhile spending a little time learning about the ways attackers can bypass 2FA. That way, you know what to look out for and can keep your accounts secure!
