Last updated on April 24th, 2023 at 11:55 am
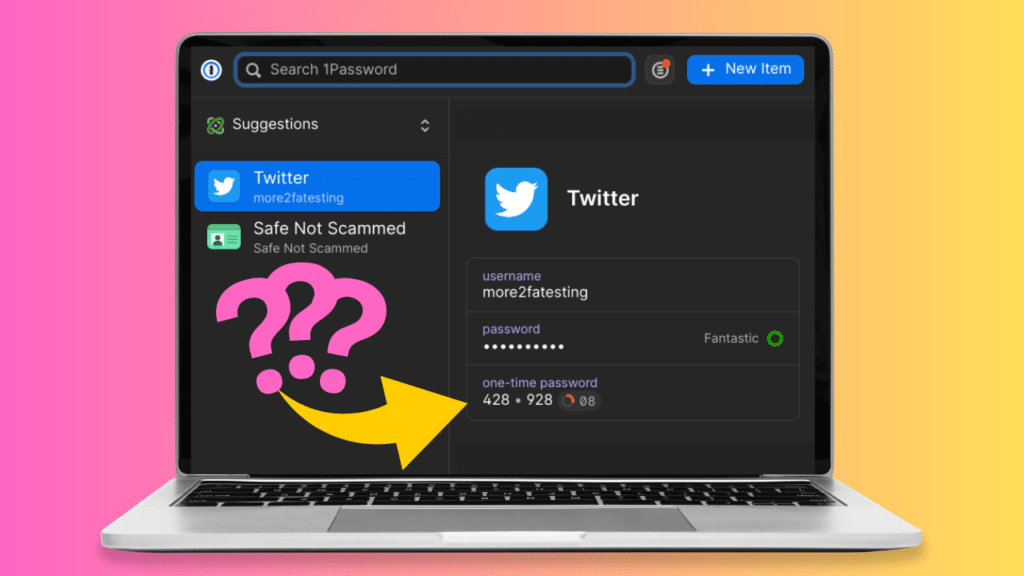
To keep your accounts as secure as possible, you’ll want to make sure you’re using a strong password and have two-factor authentication (2FA) turned on. Some password managers help you take care of both by serving not just as a password manager, but as an authenticator to secure your other online accounts as well.
But is it a good idea to use your password manager’s built-in authenticator? It depends. Doing so can be extremely convenient, but it comes with a risk: If anyone gains access to your password vault, they’ll have not just all your passwords, but all of your 2FA codes as well. You’ll have to decide based on your own personal circumstances whether the benefits outweigh the risks in your case. So let’s look at the pros and cons in more detail.
The pros of using your password manager’s built-in authenticator
If you already use a password manager like 1Password or Bitwarden, making use of their built-in authenticator can be extremely convenient.
Most password managers have a way to streamline the process of entering the 2FA codes they generate. For example, 1Password will autofill them for you, while Bitwarden will copy them to your clipboard, so all you have to do is paste them. That certainly beats looking up the code in a separate authenticator app on your phone and rushing to type it in before it expires.
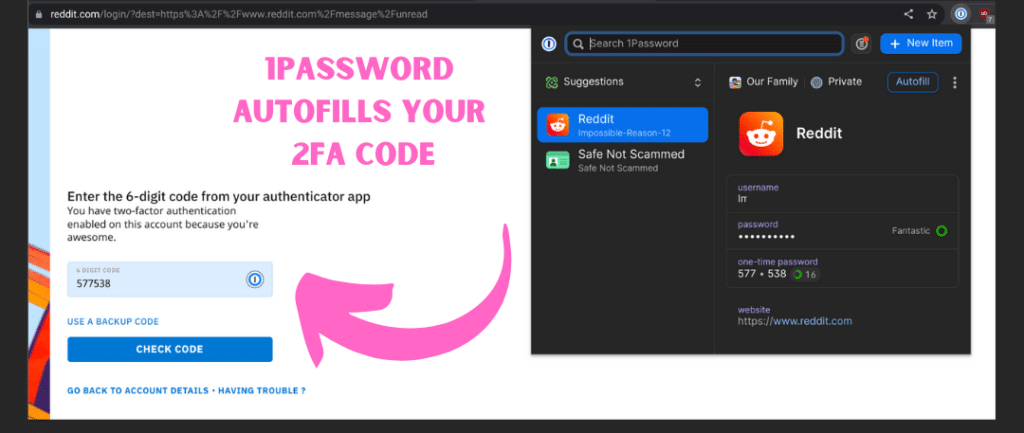
Password managers also make it easy to back up and sync your data. This means your 2FA codes aren’t lost if you lose or break your phone. It also means you can access your 2FA codes wherever you need them, be it on your computer or on your phone. While some dedicated authenticator apps, like Authy, also have these features, many do not. Google Authenticator, for example, has limited backup options and has no sync feature. And while Microsoft Authenticator offers cloud backup, it lacks a sync option.
Finally, using your password manager as an authenticator app means you don’t need to download yet another app and learn how to use it. You can just use one you already have and are familiar with.
The cons of using your password manager’s built-in authenticator

The downside of using your password manager’s built-in authenticator app is that it puts all your security eggs in one basket. With your passwords and 2FA codes stored in one handy location, all an attacker needs to do to take over your online accounts is get into your password manager.
Unfortunately, hackers have plenty of tricks to gain access to your password vault. They can try to trick you into logging in on a phishing page, for example, and can even bypass most forms of 2FA.
Alternatively, they can target the company that makes your password manager. This happened to LastPass and the attackers now have their users’ encrypted password vaults and all the time in the world to crack them.
Reducing the risk of using your password manager’s built-in authenticator
If you do want to use your password manager’s built-in authenticator, you can take precautions to minimize your risk.
First, practice good password manager security hygiene (you should do this even if you don’t use the built-in authenticator!). This means setting a strong master password and protecting your vault with 2FA.
For your master password, you’ll want something long (think 14 characters or more), unique, complex, yet easy for you to remember and type. If that sounds impossible, try coming up with a zany sounding nonsensical sentence. You’ll be surprised at how easily they stick in your mind. Here’s an example (though obviously don’t use this exact one):
2-Sad-Hamburgers-Danced-Beautifully
I ran this example through Bitwarden’s Password Strength Checker Tool, which confirmed that it was strong and would take centuries to crack. For more guidance about your master password, you can check out Bitwarden’s advice here.
In terms of 2FA for your password manager, security keys are the best option, as they are the most secure. You could also use an authenticator, but you’d need to use an external one, rather than the built-in one, otherwise you might lock yourself out of your password vault.
You’ll also need to pay close attention to the URL whenever you log in to your password manager on the web. That’s because an incorrect URL may be the only sign you’re actually on a phishing page. So make sure the URL is exactly correct before logging in.

If you’re really serious about security, you could take things even further by peppering the passwords for your most important accounts. This means that you don’t give your password manager the full passwords for these accounts. Instead, your password manager saves part of the password, but you need to add some extra characters, called the pepper, to complete it.
Say, for example, I use my password manager to generate a password for my Twitter account and it comes up with this: Y2L@q$WF*saVgL. Instead of using this as is, however, I add ‘&FUem’ to the end and use the whole thing ‘Y2L@q$WF*saVgL&FUem’ as my password. However, I only save the first part in my password manager and have to remember to add the ‘&FUem’ part manually after the first part has been auto-filled.
The great thing about this approach is that even if a hacker gets into your password vault, they won’t have the full passwords to your critical accounts. This means they won’t be able to log in to them, even if you also store your 2FA codes in your password manager.
Finally, if you want to make use of your password manager’s built-in authenticator but still feel queasy about putting all your eggs in one basket, you could decide to use it just for your less critical accounts. For example, you might feel comfortable using the built-in authenticator for your accounts on news and discussion sites, but not for your primary email or shopping accounts. In that case, you could use an external authenticator or security keys to secure your more important accounts.
The takeaway
Using your password manager’s built-in authenticator app can be very appealing due to how convenient it is. But it does come with added risk, as anyone who gains access to your password manager will have your 2FA codes and your passwords. Following good security practices, peppering your passwords, and only using the built-in authenticator for your less valuable accounts can all reduce your risk. In the end, you’ll need to decide for yourself what you are comfortable with.
