Last updated on January 15th, 2024 at 04:21 am

Scammers are impersonating buy now, pay later provider Afterpay in smishing attacks, a form of phishing sent via text messages. The scam texts try to lure victims with claims they have thousands of dollars’ worth of store credit, but victims risk losing everything in their bank accounts.
In this post, I’ll examine one such fraudulent text, pointing out red flags that indicate it’s a scam. I’ll also use an online virtual sandbox to show you exactly what happens if you fall for it.
The scam text
A redditor on the scams subreddit received the following text, claiming to be from Afterpay:
“Your 3,000 AUD instore Afterpay credit has yet to be claimed please head to afterpay-team[.]com with the reference below Ref # 100116757390”
BigFuggen on r/Scams
At first glance, the text might look convincing. But on closer inspection, there are warning signs it’s a scam.

The first warning sign is that it’s offering free money. And not just a small amount, either, but 3,000 AUD (1,900 USD) worth of free money. This means it falls under the category of “too good to be true” and should instantly raise suspicions.
The second warning sign is the link it tries to get you to click: afterpay-team[.]com. (Note: I’ve put square brackets around the dot to prevent people from accidentally visiting the site). This is not Afterpay’s official URL, which is www.afterpay.com.
Scammers often try to register domains that contain a real company’s name, e.g. realcompany-help.com, to trick you into thinking they are associated with the company even though they are not.

Scammers may also try to trick you by using a real company’s name with a different top-level domain (the bit that comes after the dot). For example, if the correct URL is realcompany.com, scammers might register realcompany.online or realcompany.biz to make themselves seem legitimate.
So, don’t trust a domain just because it contains the name of a real company. Double check the legitimate domain to make sure you’re going to the right place!
Another red flag to look out for when it comes to domains is the date it was registered. To find this out, you can do a free WHOIS lookup. There are plenty of sites online that you can use for this, though I like Whoxy as it presents the information in a very easy-to-read way.
If the WHOIS data shows that domain was registered very recently (e.g. within the past couple of months), then you should again be suspicious of it. That’s because scam sites are often short-lived as they get detected and shut down. The scammers then just register a new domain and start the process all over again.
![Screenshot from Whoxy.com showing the WHOIS information for afterpay-team[.]com. The domain was registered on October 3rd 2023.](https://safenotscammed.com/wp-content/uploads/2023/10/whoxyafterpay.png)
Doing a WHOIS lookup for afterpay-team[.]com, we see it was registered on October 3rd, which was the day before it was used in the fraudulent text posted on Reddit. Fortunately, that domain is now suspended, which you can see from the “clientHold” entry in the “Domain Status” section.
The final warning sign in the fraudulent text message is the poor grammar. Well-known companies proof-read their messages before they are sent, making spelling and grammar errors unlikely. However, the fraudulent Afterpay text is not grammatically correct—it’s just one long run-on sentence.
But what if you didn’t notice the warning signs and clicked the link? How does the scam actually work? Let’s take a look!
The scam website
I did not visit the scam site directly on my device, as doing so can be dangerous. Instead, I used an online sandbox called Any.Run to visit the site using a virtual machine.
When the fraudulent site loaded in Any.Run, it looked like this:
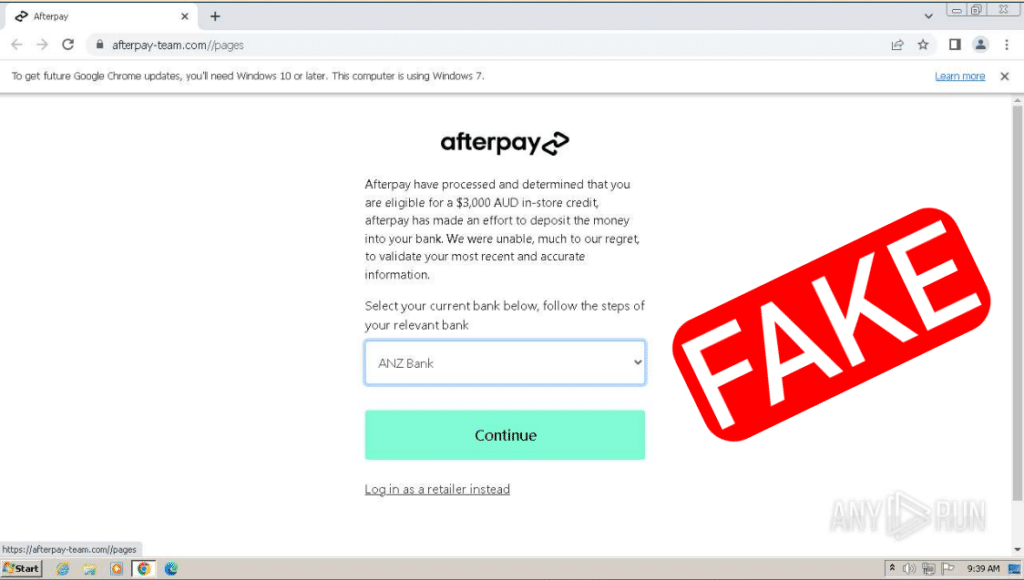
Its text read: “Afterpay have processed and determined that you are eligible for a $3,000 AUD in-store credit, afterpay has made an effort to deposit the money into your bank. We were unable, much to our regret, to validate your most recent and accurate information.”
Just like the text message, this statement has grammatical errors which give away the site’s fraudulent nature.
The scam site then provided the following instructions: “Select your current bank below, follow the steps of your relevant bank.”
The site listed the following Australian banks as options in a drop-down box: ANZ, St. George, Westpac Online Banking and NAB Bank.
![Browser window displaying a ANZ banking phishing page. The image is edited to highlight the URL, which is afterpay-team[.]com//pages.](https://safenotscammed.com/wp-content/uploads/2023/10/fakeanzannotated-1024x577.png)
Once I selected a bank, the scam site opened a new tab, displaying what looked like the bank’s login page. However, the URL was NOT the bank’s. Instead, it was https://afterpay-team[.]com//pages. This meant that any banking credentials entered on that page would be stolen by the scammers. Sophisticated phishing pages can even be set up to defeat two-factor authentication (2FA), though I don’t know if this phishing site was set up that way.
With stolen online banking credentials, the scammers could make purchases using the victim’s account or simply transfer money to themselves. Big yikes!
What to do if you fall for a similar smishing attack

If you’ve fallen for a scam like this, immediately change your online banking password if you can still log in to your account and set up 2FA if you haven’t already. Then check to see if there are any unauthorized transactions or changes to your account. The scammer may have changed the email and phone number to ones they control, for example.
You should also call your bank immediately, tell them you fell victim to a smishing attack, and ask for their help in securing your account.
If you used your old online banking password for other accounts, make sure to change your passwords there as well. You’ll want to use a strong, unique password for each account. The best way to do this is by using a password manager. Bitwarden and Proton Pass both have free plans that are worth looking into.
Finally, keep an eye on your bank account in the weeks and months following the attack to make sure there are no unauthorized transactions. If you see anything that doesn’t look right, get back in contact with your bank right away.
How to protect yourself from a smishing attack

The best way to protect yourself from smishing attacks is to learn the warning signs of a scam text message. These include:
- Appeals to emotion. Scammers often try to appeal to your emotions to make you less likely to think critically and more likely to do as they say. So, beware of texts telling you exciting news (e.g. you’ve received a big in-store credit) or telling you that something bad has happened (e.g. your account has been hacked).
- Unofficial links. Scammers try to get you to click links to steal your personal information or download malware onto your device. So, don’t click a link in a text message unless you know for sure that it is the real deal. And watch out, because the scammers may register a domain that is very similar to the real one to trick you into thinking it is legitimate.
- Spelling and grammatical errors. Watch out for poor spelling and grammar in text messages you receive. Big companies are not likely to make such mistakes in their texts, but scammers are.
If you receive a text and are not sure if it’s a scam, check with the company that supposedly sent it. But make sure you find the company’s contact details from a legitimate source (like the official website), rather than the text you received.
The takeaway
Scammers have been impersonating buy now pay later providers to trick you into giving them access to your bank account. To avoid these scams, watch out for texts that appeal to your emotions, include links to unofficial sites, or contain spelling and grammar errors. And always, always, always double check the URL is correct before entering your online banking username and password. Stay safe out there!
