Last updated on June 22nd, 2023 at 03:55 pm

Enabling two factor authentication (2FA) on your accounts is one of the best ways to keep them safe. But 2FA is not bulletproof. In this post we’ll look at four ways cybercriminals can bypass it and what you can do to protect yourself.
How secure is 2FA?
Let’s start with a reminder about how 2FA works. When it’s enabled, logging in to your online accounts has an extra step. After entering your username and password, you then have to verify your identity in another way. For example, you might need to enter a code texted to you or displayed in an app, approve a push notification sent to your phone, or push a button on a physical security key.
Without completing that extra step, an attacker should be unable to break into your account, even if they have your username and password. This makes your account much more secure.
But, as more people are enabling 2FA to protect their accounts, cybercriminals are adapting and finding ways to overcome the protection it provides.
Worryingly, many people seem unaware that attackers have tricks for getting past 2FA. According to a small study I ran on the survey platform Prolific, 30.8% of people were not familiar with any of the four methods for bypassing 2FA I’ll talk about in this post. Another 34.6% were familiar with only one of them.
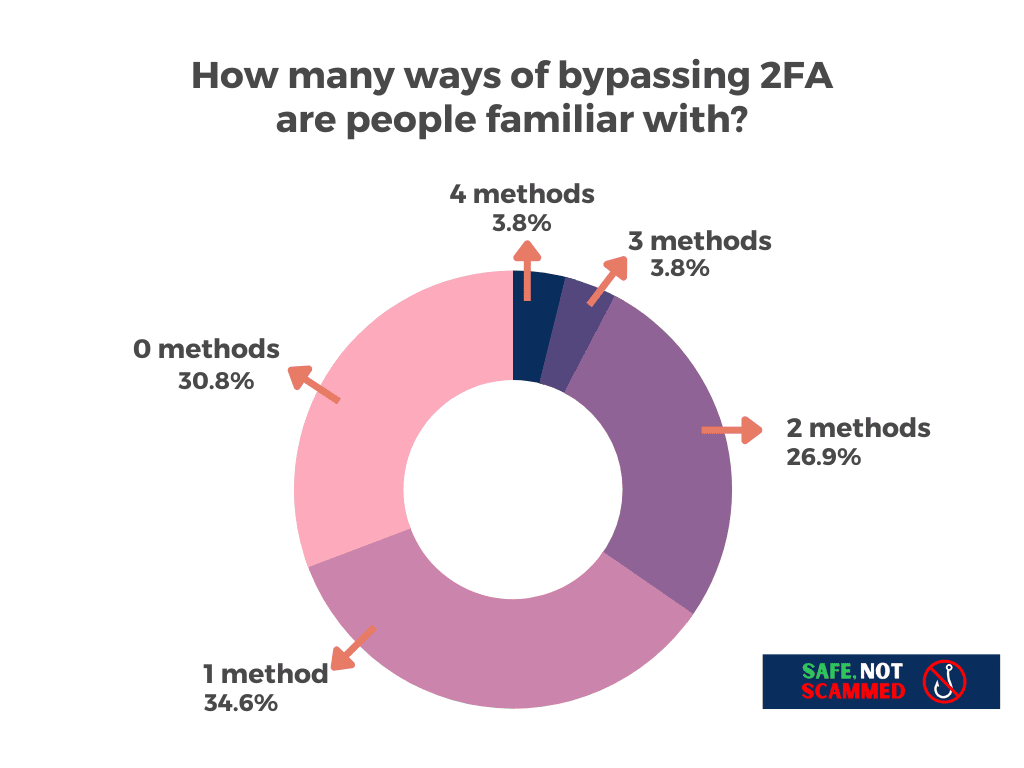
This is problematic because if you don’t know some of the sneaky ways cybercriminals can get past 2FA, you aren’t in a good position to defend yourself against them.
So, let’s take a closer look at four ways cybercriminals can bypass 2FA and what you can do to stay safe from their attacks.
SIM-Swaps

Sim-swapping is a way hackers can gain access to 2FA codes sent via texts or voice calls. In a SIM-swap, an attacker convinces your mobile carrier to transfer your number to their phone. They can do this by impersonating you and telling your carrier your phone was lost or stolen or by paying corrupt employees to make the transfer.
If they are successful, the attacker will receive all the calls and texts meant for you, including any 2FA codes sent via these methods. It also means they can change your password for services that allow password resets via text.
If the attacker resets your password or gets their hands on it in another way, e.g. by finding it in a data breach, they then have everything they need to take over your account.
So, how can you protect yourself? If you can, opt for a more secure form of 2FA. 2FA using a physical security key is the most secure you can get. Authenticator apps and push notifications are also not vulnerable to SIM-swaps, as they are not tied to your phone number.
Sometimes, though, a service doesn’t give you the option to use a more secure form of 2FA. In that case, contact your carrier and ask if you can set up a PIN or a passcode that you need to give before your number is transferred. That will make it harder for an attacker to dupe your carrier into giving them control of your number, though it won’t help if the hacker is bribing employees.
Alternatively, as recommended by Vice, you can see if your accounts will allow 2FA with a Google Voice number. A Google Voice number isn’t associated with a SIM-card, so it can’t be SIM-swapped. The number could be transferred if an attacker gets access to your Google account, but fortunately Google allows you to lock your account down with secure methods of 2FA, such as a hardware key.
Push-bombing

Push-bombing is a strategy attackers use to break into accounts that receive 2FA push notifications. The idea behind the attack is simple: hackers repeatedly attempt to login to your account using the correct credentials, perhaps obtained via data breaches or phishing, and generate multiple push notifications, hoping you will approve one of them.
Whether people approve the notifications by accident or to make the barrage of notifications stop, push-bombing attacks are incredibly effective. For example, members of the hacking group Lapsus$ used it to break into employee accounts at big companies, including Microsoft, Okta and Uber, and pilfer their data.
So, how can you avoid falling victim to a push-bombing attack? If you receive multiple 2FA push notifications, assume someone is trying to break into your account and don’t approve them. Instead, change your password and, if it’s a work account, contact your IT department.
Even if you don’t receive a barrage of 2FA push notifications, it’s a good idea to pay attention to every one you receive to make sure nothing is amiss. Each one should include information about the sign-in attempt that generated it, such as the IP address or location. If anything seems sketchy, don’t approve the notification and change your password just to be safe.
Phishing

In a phishing attempt, an attacker sends you an email or a text claiming there is an urgent issue with your account and provides you with a link to login and “resolve” it. The link, however, takes you to a fraudulent website rather than the legitimate one and logging in gives the hackers what they need to break into your account.
Tools called Man-in-the-Middle phishing kits, such as Evilginx, allow attackers to create sophisticated phishing campaigns. Phishing sites developed with these tools display live pages from the websites they impersonate and intercept data sent between your computer and the real site. This means there is no sign these sites are not legitimate, unless you pay attention to the URLs and notice they are not correct. It also means these sites can bypass most forms of 2FA.
If you enter your username and password into one of these phishing sites, you’ll be prompted to authenticate with your second factor. Unless you use a physical security key, everything will work as expected and you’ll successfully log in.
The real site will then send your computer what’s known as a session cookie, which allows you to stay logged in. As the phishing site intercepts the data sent between you and the real site, it saves the session cookie for the attacker to use. By adding it to a browser they control, the attacker tricks the real site into thinking they have already authenticated, meaning they gain instant access to your account, with no username, password, or 2FA required.
How do you protect yourself against this kind of attack? One way is to use a hardware key for your second factor, since they will not authenticate a login to a phishing site, not even a sophisticated one made using a Man-in-the-Middle phishing toolkit. That’s because a hardware key knows the URL of the legitimate site and realizes the URL of the phishing site is not the same.
If you don’t have a hardware key or the services you use don’t support them, you’ll want to pay close attention to the URL of the sites you log in to. Check the domain is correct, e.g. that you’re logging into google[.]com and not g00gle[.]com. A password manager can help with this, since they won’t autofill your credentials into a site with the wrong URL.
Malware

Downloading an attachment from an email, plugging in a questionable flash drive, or clicking on a malicious ad can all result in a malware infection. While there are all kinds of malware, information stealers are growing in popularity as they can be used to bypass 2FA.
Information stealers, true to their name, grab your personal information and send it to criminals. This type of malware looks for data like your passwords, bank and credit card details, crypto wallet information, and cookies.
It’s the cookie-stealing capabilities of information stealers that make them a tool criminals can use to bypass 2FA. As we saw with phishing, once a criminal gets hold of your session cookie, they can add it to their browser and gain instant access to your account, with no username, password or 2FA required.
How do you protect yourself from cookie-stealing, 2FA-bypassing malware? First, think carefully before downloading any new programs. Ask yourself: Is the software reputable? And does it come from a source you trust?
Even if you are downloading well-known and trusted software, double check you’re downloading it from the official website. Cybercriminals often create fake sites for popular software to trick people into downloading their malware. Worse, they purchase ads so their fake sites appear at the top of Google’s search results for that software. Installing an ad blocker will hide these ads so you don’t accidentally download something nasty.
Finally, good anti-malware software can prevent any malware you do accidentally download from getting its claws into your system.
The takeaway
2FA is still one of the best ways to protect your online accounts, but it’s not infallible. Being aware of the ways cybercriminals can bypass it can help you avoid falling prey to their attacks and ensure your accounts stay secure.
