Last updated on May 8th, 2024 at 11:47 pm

The fallout from ransomware gang Cl0p’s massive, worldwide attack continues to grow. Police departments, state and federal agencies, and numerous companies are among the known victims.
Recap
Cl0p stole data from hundreds of organizations by exploiting a vulnerability in popular file transfer software MOVEit at the end of May. The cybercriminals then told organizations to contact them to negotiate the cost of deleting their stolen data. If companies failed to do so or could not reach a deal, Cl0p warned it would publish their stolen files on its data leak site.
Earlier this month, companies including the BBC and British Airways disclosed they were hit by the attack after their payroll provider, Zellis, was breached.
The Minnesota Department of Education and the States of Illinois and Missouri also reported that they had been affected by the hack.
Cl0p then began naming organizations who had not been cooperating on its data leak site on June 14th.
Last week’s developments
On Thursday last week, Louisiana’s Office for Motor Vehicles (OMV) and Oregon’s Department of Transportation (ODOT) disclosed their data had been accessed in the MOVEit attack.
ODOT warned “the accessed data contained personal information for approximately 3.5 million Oregonians.” The agency added, “individuals who have an active Oregon ID or driver’s license should assume information related to that ID is part of this breach.”
Similarly, OMV reported “all Louisianans with a state-issued driver’s license, ID or car registration have likely had” their personal information exposed in the breach.
But it’s not just state agencies that have been affected. The Cybersecurity and Infrastructure Security Agency (CISA) disclosed on Thursday that federal agencies have been breached by the MOVEit attack as well. While the full number of agencies is not yet known, the Department of Energy confirmed it had been caught up in the breach.
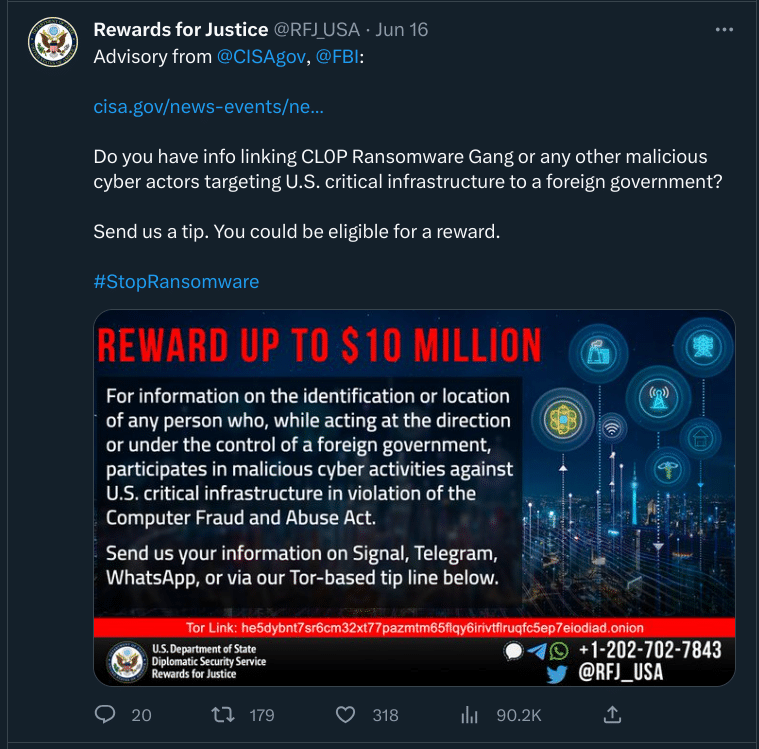
The US government is keen to identify the threat actors behind Cl0p. The US State Department’s Rewards for Justice program tweeted out a request for tips on Friday “linking CL0P Ransomware Gang … to a foreign government.” Tipsters with useful information could stand to receive up to $10 million in rewards.
This week’s developments so far

On Monday this week, the Metro Vancouver Transit Police revealed its data had been breached “during a cyber attack on MOVEit.” While the police department did not mention Cl0p by name, the ransomware gang is currently the only group linked to the MOVEit breach.
The police force disclosed that 186 of its files had been accessed and that it was reviewing “what information is contained within” them. It added that it did not anticipate the breach to impact “police investigations or prosecutions.”
Meanwhile, Cl0p has continued to name organizations who are not cooperating with the negotiation process on its leak site.
Eleven companies were added on Monday alone. According to data from ecrime.ch, the named companies come from a variety of industries, including banking and financial services, computer and network security, construction, education, insurance, IT, marketing and manufacturing.
Other as yet unnamed companies are presumably negotiating with Cl0p to prevent their names and data from being released. If negotiations fail, their information will ultimately be published on Cl0p’s leak site, too.
