Last updated on May 8th, 2024 at 11:46 pm

Educational organizations are often at the top of a cybercriminal’s list of potential targets. That’s because they hold a lot of valuable data but rarely have much budget for cybersecurity. Ransomware gangs, in particular, have been aggressively targeting the sector.
In this post, I’ll dive into ransomware and the threat it poses to educational institutions, their staff and students. As part of this, I’ll present some sobering statistics from threat intelligence service ecrime.ch. Then I’ll look at what’s being done to defend educational institutions against this threat.
You can also check out the infographic accompanying this post below or download a higher quality version of it here.
What is ransomware?
Traditional ransomware is malware that encrypts files on an infected device, making it impossible for the victim to open or use them. The cybercriminals responsible for the malware would then demand the victim pay a ransom to decrypt their files and make them usable again.
As the threat of ransomware became more well known, however, companies began backing up their data so they could restore their files without paying a ransom. Groups of cybercriminals responsible for the malware, known as ransomware gangs, saw their profits dwindling and so adopted a new strategy.
Instead of just encrypting files, the criminal gangs started stealing a copy of them, too. They then threatened to release the stolen data onto the dark web unless the ransom was paid. Some gangs have since completely stopped encrypting files, focusing instead on data theft in a “pure extortion” approach.
A rising threat to educational organizations
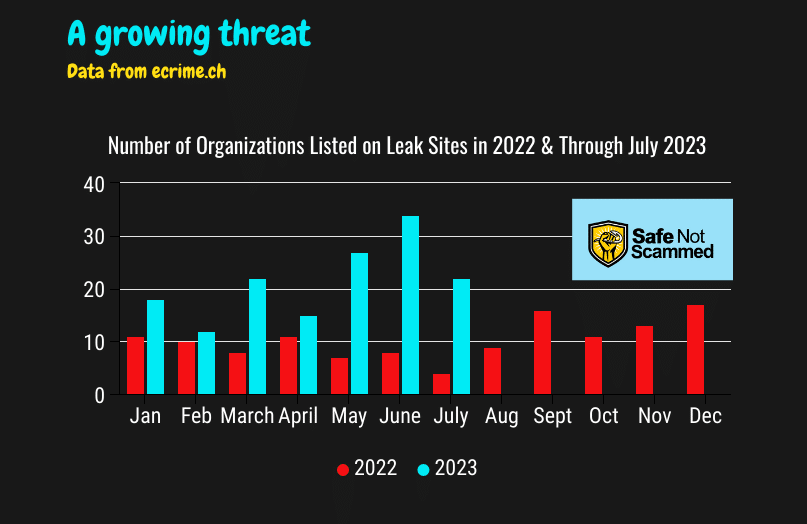
According to data from ecrime.ch, ransomware gangs listed 125 educational organizations on their data leak sites in 2022. Between January and July 2023, cybercriminals had already surpassed that number, claiming 150 institutions.
As the organizations listed on dark web leak sites only include those that did not pay the ransom, at least initially, the total number of educational institutions breached by ransomware is likely much higher.
A variety of different ransomware gangs are behind these attacks. Some, such as Vice Society, specifically target educational organizations. Others, such as Cl0p, attack a wide range of industries but still hit the educational sector heavily. Some, like Royal, have attacked schools only to claim later they had a change of heart. Any such claims should be viewed with suspicion, however.
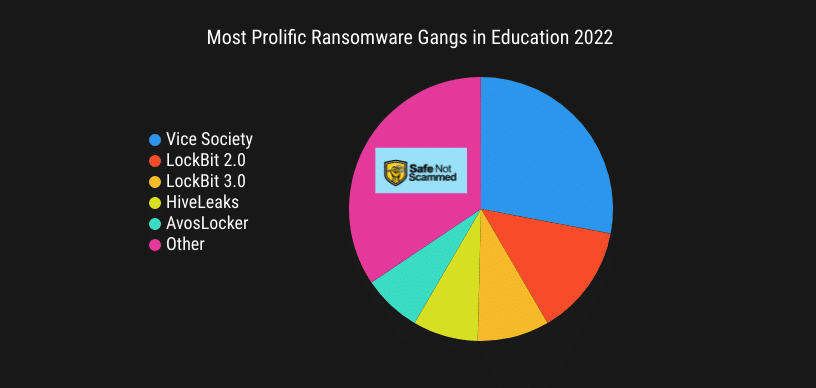
Last year, Vice Society was the most prolific criminal gang targeting educational institutions. LockBit 2.0, LockBit 3.0, HiveLeaks and AvosLocker rounded out the top five. These five gangs named 82 out of 125 educational institutions listed on leak sites in 2022.
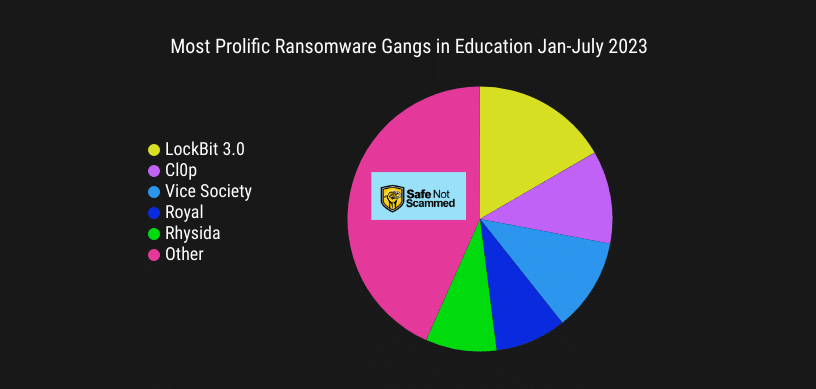
LockBit 3.0 targeted the most educational institutions Jan-July 2023. Data from ecrime.ch.
The five most prolific ransomware gangs targeting educational institutions this year are LockBit 3.0, Cl0p, Vice Society, Royal and Rhysida. Combined, they listed 85 out of the 150 educational institutions that were named on ransomware data leak sites.
The impact of ransomware on educational organizations

Ransomware attacks can cause significant harm to educational institutions and those served by them. A typical attack can disrupt education, cause data loss, financially harm the victim organization and make sensitive information public. Let’s look at each of these in turn.
Disrupting education
Schools affected by ransomware often have to cancel classes while they deal with the aftermath of the attack, disrupting students’ education. According to Comparitech, schools had an average of 11.65 days of ransomware-induced downtime in 2022.
Data loss
An educational organization attacked by ransomware may find it cannot restore all its crucial files, even if it paid the ransom. Fortunately, a recent report from Sophos found 100% of higher, and 99% of lower, educational institutions successfully recovered their data, either by using backups or paying the ransom.
However, in a different survey, Sophos found that 1 in 10 organizations (not just educational institutions) from the UK and France retrieved none of their data after paying the ransom. This is something educational institutions should keep in mind if they are considering paying a ransom.
Financial harm
Educational organizations face high costs after a ransomware attack, regardless of whether they pay the ransom. That’s because they still need to pay for labor and new devices, for example. Downtime can also cause them to incur costs by preventing them from recruiting students or wooing donors.
A report by Sophos found it cost lower educational institutions $1.59 million and higher educational institutions $1 million to recover from an attack in 2022.
Sometimes, the financial strain caused by ransomware is too much for an educational institution to bear. For example, Lincoln College was forced to close in 2022, after being unable to recover financially when ransomware brought down its systems.
Making private information public
Ransomware gangs can steal and publish sensitive data from educational institutions, putting the personal information of students and staff at risk. Unfortunately, this can have devastating consequences.
For example, the Medusa ransomware gang leaked highly sensitive information from the Minneapolis School District on both the dark and clear web earlier this year. The leaked data included reports of rape, abuse and mental health issues, as well as students’ addresses, dates of birth, and social security numbers. This has deeply violated the students’ privacy and made them vulnerable to identity theft.
Future plans

The government fortunately recognizes the threat posed by ransomware and has recently taken steps to help educational institutions defend themselves.
Last month, Jessica Rosenworcel, Chairwoman of the Federal Communications Commission, proposed a pilot program to invest $200 million over three years to help schools beef up their cyber defenses. While this is a start, experts say schools need considerably more investment to defend themselves from ransomware attacks.
More help is hopefully on the way after the White House held the very first summit on strengthening cybersecurity in K-12 schools this month.
As part of its plan to help protect schools from cyberattacks, the Biden administration announced the creation of a Government Coordinating Council to foster collaboration between the government and the education sector.
The administration also announced that a number of technology companies, including Amazon Web Services, Cloudflare and Google, were offering free or low cost services to schools to help them defend themselves.
The takeaway
Ransomware gangs are ruthlessly attacking educational institutions, harming both students and educators. The government has recently taken some much needed first steps to protect schools from this threat. However, we’ll have to wait and see if it’s enough to make a difference.
